New Malware Linked to Russian Cybercriminals: A Growing Concern
In a notable advancement in teh ongoing fight against cyber threats, Google has uncovered a novel strain of malware that is believed to be associated with a hacking group based in Russia. This discovery highlights the continuous and evolving challenges posed by state-sponsored cyber activities, which are increasingly targeting various sectors across the globe. A report from Reuters indicates that Google’s security experts have detailed the intricate characteristics of this malware and its potential ramifications for both businesses and governmental entities. As nations confront the consequences of such cyber intrusions, this finding emphasizes an urgent need for improved cybersecurity protocols and heightened awareness in our digital age.
Google Discovers New Malware Linked to Russian Hackers
In a critical update, Google has identified a new variant of malware attributed to a sophisticated Russian hacking institution known for its advanced cyber-espionage tactics. This malicious software is engineered to infiltrate unsuspecting networks, posing significant risks to both public sector institutions and private enterprises. The detection aligns with Google’s commitment to bolster cybersecurity measures aimed at safeguarding users from emerging threats within the digital realm. Experts assert that this malware could enable attackers to extract sensitive data while also disrupting essential infrastructure.
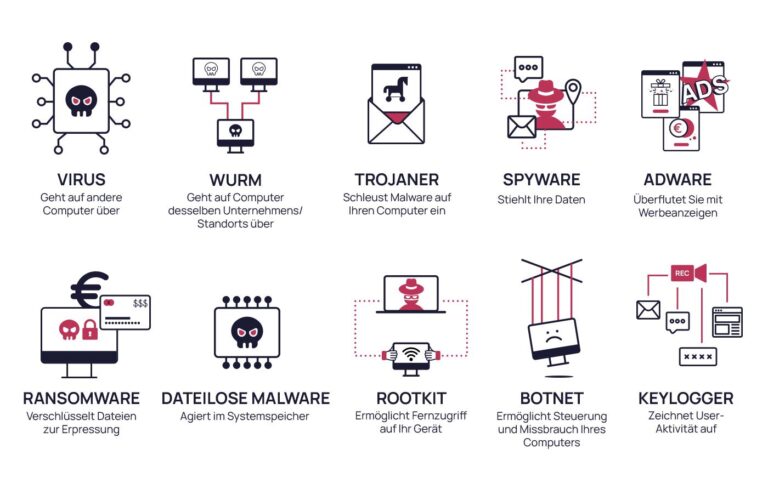
The data released by Google reveals that this malware employs sophisticated evasion techniques designed specifically to circumvent traditional security defenses. Notable features include:
- Stealth Mechanisms: Crafted to elude detection by standard antivirus solutions.
- Sensitive Data Extraction: Capable of gathering and relaying confidential information back to malicious actors.
- Remote Control Access: Grants hackers control over compromised devices from afar.
As cybersecurity professionals continue their analysis of thes findings, organizations are encouraged to strengthen their security frameworks and maintain vigilance against possible attacks. Gaining insight into the strategies employed by these hackers will be vital for developing effective countermeasures against future breaches.
Effects on Cybersecurity Landscape and Vulnerable Sectors
The recent identification of malware linked with an infamous Russian hacking group carries substantial implications for the overall cybersecurity landscape. This situation underscores an urgent need for organizations—particularly those operating within critical infrastructure or defense sectors—to enhance their cybersecurity protocols substantially. The increasing sophistication of cyber threats demands adaptive strategies which may include:
- Advanced Threat detection Systems: Implementing real-time monitoring tools capable of identifying and mitigating attacks as they occur.
- Timely Software Updates: Regularly updating systems can close vulnerabilities that might be exploited by such malicious software.
- Cohesive Training Programs: Educating employees about phishing schemes and other social engineering tactics commonly utilized in cyberattacks is crucial.
This newly discovered malware poses risks across multiple industries, particularly those handling sensitive data or high-profile operations. Key sectors likely affected include:
| Sector | Potential Consequences |
|---|---|
| Energization Sector | Possible service disruptions affecting national infrastructure integrity. |
The necessity remains clear: organizations must adopt proactive measures while implementing robust cybersecurity frameworks if they wish to stay ahead amidst evolving threats stemming from state-sponsored hacking initiatives. Neglecting adaptation could lead not only individual companies but also national security into perilous situations due to devastating breaches occurring as a result of inadequate defenses.
Strategies Organizations should Employ Against Emerging Threats
A proactive stance is essential for organizations aiming to mitigate risks associated with advanced forms of malware connected to state-sponsored hacker groups effectively . Strategies should prioritize enhancing overall cybersecurity infrastructures while fostering employee vigilance throughout all levels within each organization . Key actions may encompass :
- Routine Software Updates: Ensure all systems receive timely updates regularly closing any potential gaps exploitable through malicious programs .
- Sophisticated Threat Detection Systems: Deploy advanced monitoring technologies equipped utilizing artificial intelligence capabilities enabling rapid identification neutralization concerning emerging dangers .
- employee Training Initiatives: Conduct frequent training sessions educating staff members regarding recognizing suspicious behaviors alongside appropriate response procedures when encountering them .
- Incident response Protocols: Formulate complete incident response plans detailing specific actions required during breach events ensuring regular testing occurs maintaining effectiveness over time .
Collaboration among industry peers alongside expert partners proves invaluable staying informed regarding current vulnerabilities attack methodologies allowing collective resilience building efforts towards defending against future incursions effectively .
Consider adopting approaches like:
Tactic Description tactical Intelligence Sharing Engage actively sharing insights partnerships formed between industry counterparts keeping abreast evolving threat landscapes best practices available today . - Sophisticated Threat Detection Systems: Deploy advanced monitoring technologies equipped utilizing artificial intelligence capabilities enabling rapid identification neutralization concerning emerging dangers .